In Germany a lot of music videos on youtube are not available because youtube and GEMA could never agree on the amount of licence fees that youtube should pay to legally stream those videos. So if I want to listen / watch to a Lady Gaga Video in Germany I won’t be able to do so on youtube but rather see a message saying something like
“Sorry you requested some content which is not available in Germany.”
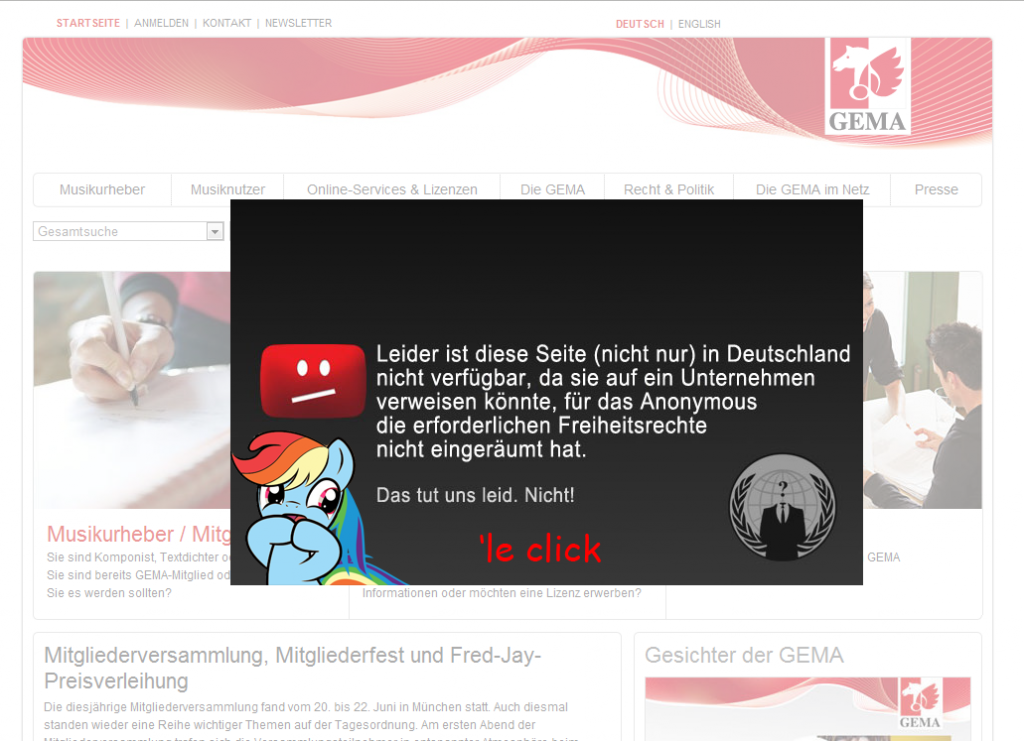
After several rounds in this battle between youtube and GEMA we have a third party entering the battle field. This morning the hacker groupd anonymous hacked the website of GEMA. if you visit the site now you will find a german message looking very similar to the message that is displayed on the youtube videos that are not available in Germany. This parody message displayed on the GEMA website roughly translated says:
“sorry this site is (not only) in germany not available, since it is conected to a company for which anonymous doesn’t like the standards of freedom. We are not sorry about this”
I am kind of excited to see how things between GEMA and youtube will develope in the future. As someone connected to music industry I can understand both sides very well. Let us see what the future for music & internet will bring. Till then I will listen to lady gaga on simfy.de
edit:
oh and by the way I just looked a little bit into the data traffic of the hacked GEMA site. the background music that is playing on the hacked gema site is an hidden youtube video on autoplay. if you wish to see the video here you go!
GEMA co-workers data base also been hacked?
I just received a chat message from a friend that it seems to be that the data base from the GEMA CMS also has been hacked or leaked to the public in some other way. I don’t know if this data is valid but it says that it displays the passwords of many people working at GEMA.
Honestly: “Who is still building IT systems that saves passwords in a non encrypted way?!?”
For anyone working at GEMA: “These passwords don’t look secure. People change your other passwords.”
The following data snippet ist taken from pastebin
(username,password,email,*plainpw*)
cdode:895cfbf5add9e56b40ee2e193de2fff9::kihnkim
testredakteur:128ecf542a35ac5270a87dc740918404::bla
….
….
….
vbley:def5ebb4aa81ae49a9847503bc942579:vbley@gema.de:07verena10
bdorn:f14f831a9badfe0af03043106af04591:bdorn@gema.de:bdorn
….
….
….
+——-+——————–+———————–+———–+——————-+———————————-+
| admin | email | realName | usergroup | username | password |
+——-+——————–+———————–+———–+——————-+———————————-+
| 1 | NULL | NULL | NULL | _cli_scheduler | f95b8ddef737a31bed2dc320e8464ffc |
| 0 | NULL | NULL | 2 | ahaberkorn | bla |
| 0 | NULL | NULL | 4 | bdorn | blabla |
| 1 | saur@aicomm.de | Rainer Saur | NULL | cdode | rsaur |
…
…
…
| 0 | NULL | www_redakteur | 2 | vbley | hilftuns |
| 0 | smai@gema.de | Sabine Mai | 5 | www_redakteur | smai |
+——-+——————–+———————–+———–+——————-+———————————-+